Salesforce contains a wealth of customer data that need proper security. Companies have to worry about common cyber attacks, along with laws and regulations that demand compliance. You may have heard of HIPAA, but what about the GDPR, PII, PCI, COPPA, or CPPA?
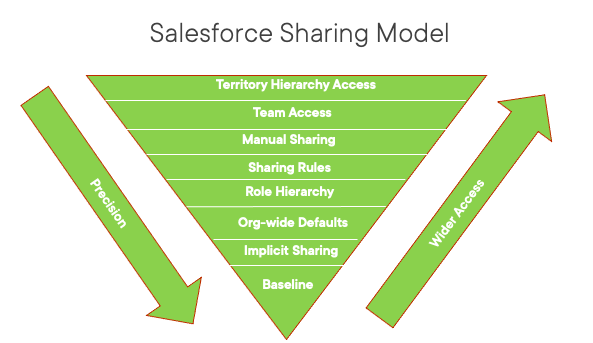
Protecting sensitive Salesforce data is an ongoing and multifaceted task. The level of protection varies by company. The first line of defense is always field and object-level permissions, along with the Salesforce Sharing Model. You can learn more about those in my Security Series.
Here are 5 additional methods to specifically help protect sensitive information in Salesforce
Encryption
Data encryption is a vital technique to protect sensitive data at rest or when it is stored. Salesforce offers two primary encryption methods: Classic Encryption and Shield Platform Encryption. Both use keys to scramble and unscramble sensitive data. Neither replace field-level security, which should always be looked at first.
Neither replace field-level security, which should always be looked at first.
Classic Encryption
Classic or Field-level encryption encrypts individual sensitive fields like SSNs. An unauthorized user will see data in the encrypted form and only users with the “View Encrypted Data” permission can view actual data.
Pros:
- Strong encryption of text fields, along with data masking
- Prevents exposure of sensitive data with a permission.
- Included with the base user license.
Cons:
- Does not encrypt existing fields or files and attachments.
- Only used for new fields using a custom field type called ‘Text (Encrypted)’
- Limited to 175 characters, along with many other restrictions.
Shield Platform Encryption
Enabling Shield Platform Encryption allows you to encrypt sensitive fields, files, attachments and more. It encrypts data at rest and in transit for strong protection. Provides the strongest and broadest level of protection for Salesforce data. But, careful consideration is needed before enabling.
Pros:
- Allows organizations to comply with regulatory and business requirements.
- Robust defense of data using a 256-bit AES key.
- Allows you to encrypt existing fields and data found in other sources.
Cons:
- Requires additional fees through an add-on license.
- Requires setup and ongoing key management.
- Does not support all Salesforce apps and some features may not work as expected.
- Only encrypts fields created or updated after encryption is enabled.
Personal Information Management
Available after the Winter 22 release, Enhanced Personal Information Management hides personal information fields on user records for external users (community or site users). Fields like SSN’s and credit card numbers are replaced with asterisks or custom masks.
Pros:
- Limits exposure of sensitive data without additional permissions.
- Simple to configure field-level settings.
- Can secure up to 20 fields you select.
Cons:
- Only partially hides data and is not the same as data masking.
- Less flexible and secure than full encryption.
Data Masking
Data masking fully obscures sensitive data by replacing it with fictional but realistically formatted data. For example, allows testing sandboxes with masked copies of real data. Installed with a managed package.
Pros:
- Fully hides actual sensitive data with fictional data.
- Great protection for hiding data when working with outside contractors and sandboxes.
Cons:
- Disables custom workflow rules and triggers
- Complex to set up and manage.
Data Classification Fields
Create standard data classification fields, such as Compliance Categorization, Data Owner, Data Sensitivity Level and Field Usage. Allows you to classify sensitive data and understand how it is being used. Works great with Shield Platform Encryption to encrypt fields only when necessary.
Pros:
- Simple classification system indicating sensitive info.
- Can run SOQL queries and create reports on classification data.
Cons:
- Does not secure data, just provides visual labels for awareness.
Monitoring
Protecting your sensitive data does not mean it is always secure. It is necessary to monitor user activity to look for suspicious activity and take action, if necessary. Tracks up to fifty event types, such as logins, API calls, report exports and Apex executions. Salesforce offers two ways to tracks events: traditional Event Monitoring and Real-time Event Monitoring.
Event Monitoring
Traditional Event Monitoring works with the Event Monitoring Analytics App to monitor event log files and draw insights from the data. It can not only monitor suspicious activity, but help to optimize performance by examining slow page performance.
Pros:
- Includes pre-built reports and dashboards to monitor different event types.
- Use the Event Monitoring Analytics App to share and monitor key performance indicators (KPI’s)
- Works with Transaction security to block certain user actions and send notifications when certain events occur.
Cons:
- Only monitors data within a 24 hour time period and must be done manually.
- Works with API and complex alert configuration required.
Real-time Event Monitoring
Real-time Event Monitoring is used to monitor user activity in your Salesforce organization in near real-time. Does this though the use of a application monitoring service. Working with Transaction Security, policies can be created to send notifications and perform certain actions.
Pros:
- Able to take action sooner that traditional event monitoring
- Works with Platform Events, so you can subscribe to events published by Salesforce.
- Query events stored in a big object with SOQL and batch Apex.
Cons:
- Requires purchase of an add-on license.
- Complex alert configuration required.
Each method for protecting sensitive Salesforce data has its own strengths and weaknesses. The best approach often involves a combination of these techniques to create a robust security framework. The key is to strike a balance between security and usability, ensuring that sensitive data remains protected while enabling users to work efficiently. Keep in mind that security is not a one-time effort but an ongoing process that should evolve alongside your organization’s changing needs and the ever-evolving threat landscape.



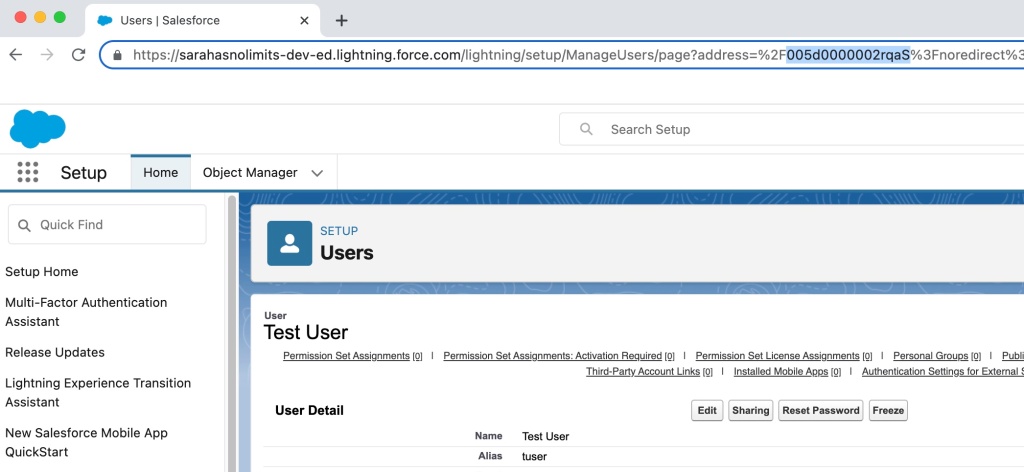

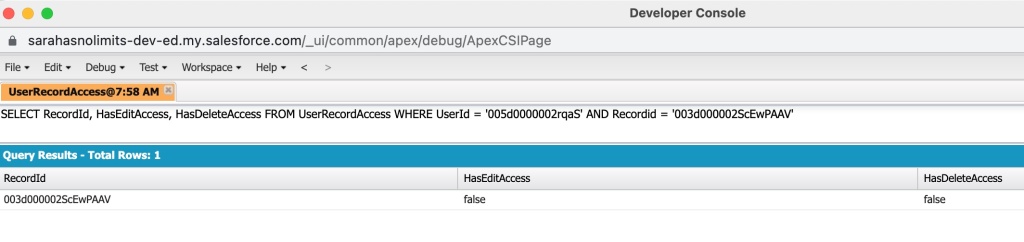
 in Salesforce and clicking Developer Console. This brings up a new window. From the Query tab, you can type in your query using the ID’s gathered in the first two steps. Click Execute to run the query.
in Salesforce and clicking Developer Console. This brings up a new window. From the Query tab, you can type in your query using the ID’s gathered in the first two steps. Click Execute to run the query.